Navigating Networks with Ease: A Comprehensive Guide to Mapping Network Drives
Related Articles: Navigating Networks with Ease: A Comprehensive Guide to Mapping Network Drives
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Navigating Networks with Ease: A Comprehensive Guide to Mapping Network Drives. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Navigating Networks with Ease: A Comprehensive Guide to Mapping Network Drives
- 2 Introduction
- 3 Navigating Networks with Ease: A Comprehensive Guide to Mapping Network Drives
- 3.1 Understanding the Concept of Mapping Network Drives
- 3.2 The Power of Command-Line Mapping: Flexibility and Control
- 3.3 Command-Line Syntax: Deciphering the Language of Mapping
- 3.4 Illustrative Examples: Mapping Network Drives in Action
- 3.5 Benefits of Mapping Network Drives: Streamlining Network Access
- 3.6 FAQs Regarding Mapping Network Drives
- 3.7 Tips for Effective Network Drive Mapping
- 3.8 Conclusion: Unlocking Network Potential with Mapping
- 4 Closure
Navigating Networks with Ease: A Comprehensive Guide to Mapping Network Drives
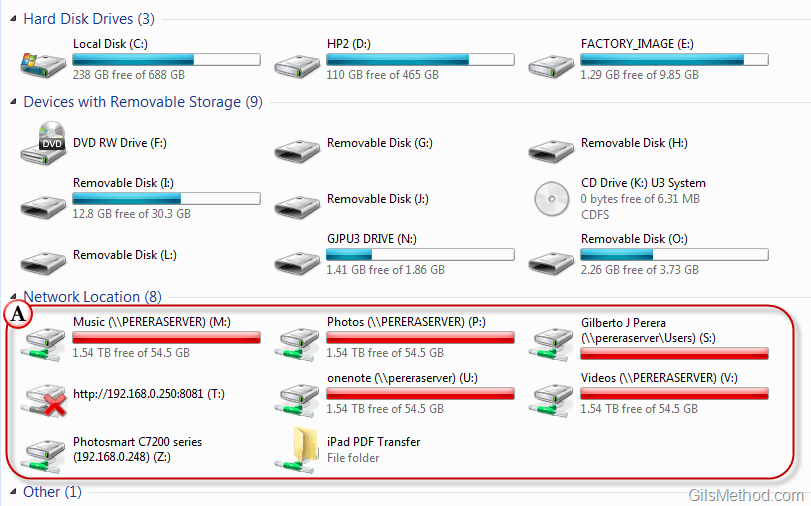
In the realm of computer networking, seamlessly accessing resources located on remote machines is paramount. While file sharing protocols like FTP and SMB offer methods to transfer data, the concept of "mapping a network drive" emerges as a powerful and convenient tool for navigating and interacting with shared resources on a network. This process, often executed through command-line interfaces, establishes a persistent connection to a specific network location, allowing users to access its contents as if they were directly on their local machine.
Understanding the Concept of Mapping Network Drives
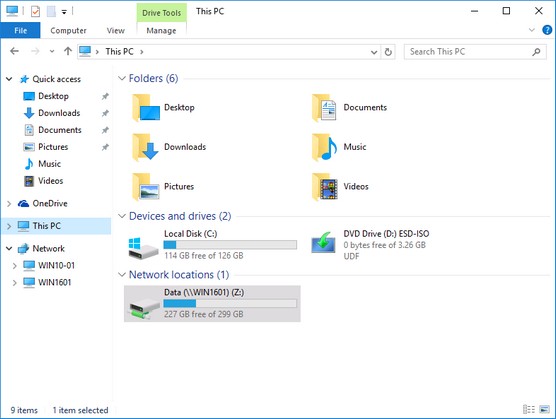
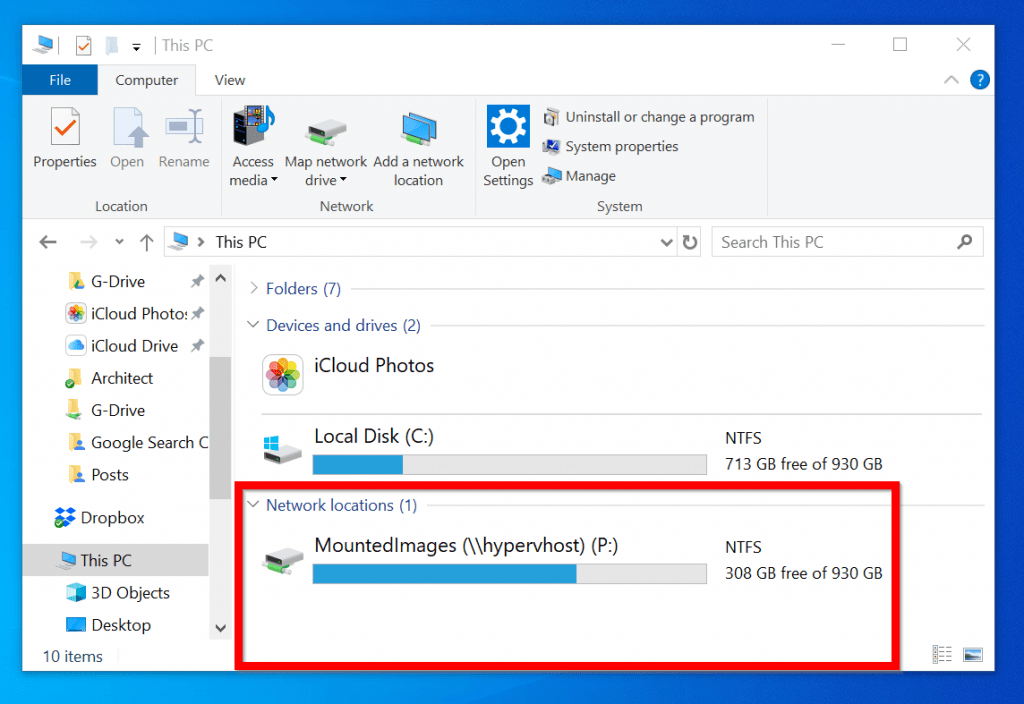
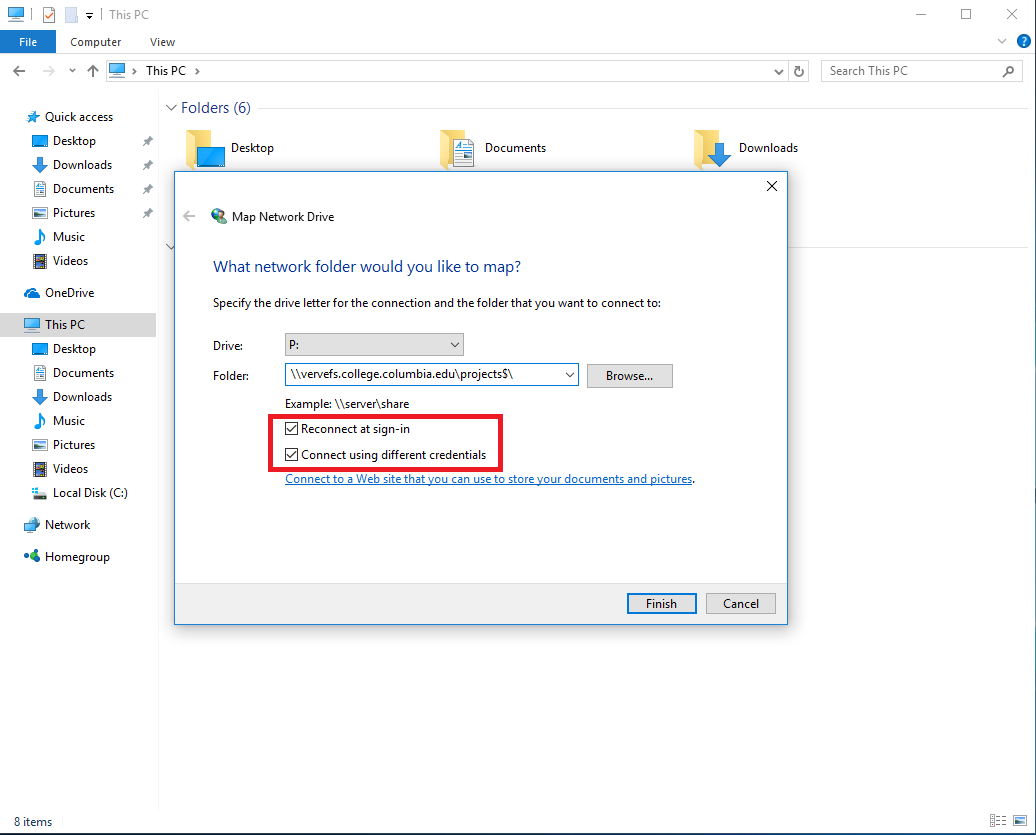
Imagine a scenario where you frequently need to access files stored on a server in your office network. Instead of manually typing the server’s address and navigating through folders each time, mapping a network drive simplifies this process. Mapping essentially creates an alias, a virtual representation of the remote location, accessible through a familiar drive letter on your computer. This virtual drive letter acts as a gateway, allowing you to browse, open, and modify files stored on the server as if they were on your local hard drive.
The Power of Command-Line Mapping: Flexibility and Control
While graphical user interfaces (GUIs) offer a user-friendly approach to mapping network drives, command-line interfaces provide a more granular level of control and flexibility. This is particularly beneficial for system administrators and power users who need to manage multiple network drives or work in environments where GUI access is limited.
Command-Line Syntax: Deciphering the Language of Mapping
The syntax for mapping network drives using command-line interfaces varies slightly depending on the operating system. However, the core components remain consistent:
- Command: The specific command used to initiate the mapping process. This typically includes keywords like "net use" (Windows) or "mount" (Linux/macOS).
- Drive Letter: The desired drive letter for the mapped network drive. This must be a valid, unused drive letter on your system.
- Network Path: The complete address of the shared resource on the network. This typically includes the server name or IP address, followed by the share name.
- Credentials: In cases where the network drive requires authentication, you may need to provide a username and password.
Illustrative Examples: Mapping Network Drives in Action
Let’s delve into concrete examples to solidify the concept of mapping network drives through command-line interfaces:
Windows:
net use Z: serversharename /user:username passwordThis command maps the network share "sharename" located on the server "server" to the drive letter "Z". The "/user:username password" option provides the necessary credentials for accessing the shared resource.
Linux/macOS:
sudo mount -t cifs //server/sharename /mnt/sharename -o username=username,password=passwordThis command uses the "mount" command to map the "sharename" located on the "server" to the directory "/mnt/sharename". The "-o" option specifies the username and password for authentication.
Benefits of Mapping Network Drives: Streamlining Network Access
The advantages of mapping network drives are multifaceted:
- Simplified Access: Mapping eliminates the need to manually navigate through network paths, allowing users to access shared resources with ease.
- Enhanced Productivity: By providing a direct, persistent connection, mapped drives streamline workflows, especially when dealing with large files or frequent access to shared data.
- Centralized Data Management: Mapping promotes a centralized approach to data storage, enabling users to access files from various locations on the network.
- Streamlined Collaboration: Mapped drives facilitate seamless collaboration among team members by providing a common access point for shared resources.
- Security Enhancement: By utilizing authentication mechanisms, mapping network drives can enhance security by restricting access to authorized users only.
FAQs Regarding Mapping Network Drives
1. Can I map a network drive without a password?
While it is possible to map a network drive without a password if the share is publicly accessible, it is generally not recommended for security reasons. Using a password ensures that only authorized individuals can access the shared resources.
2. What happens if the network drive is unavailable?
If the network drive becomes unavailable, you may encounter errors when trying to access it. The mapped drive letter will remain, but accessing its contents will result in an error message.
3. Can I map a network drive on a different operating system?
Yes, mapping network drives is possible across different operating systems, but the specific commands and syntax may vary. Refer to the documentation for your operating system to understand the appropriate commands.
4. Can I map multiple network drives?
Yes, you can map multiple network drives to different drive letters on your computer. This allows you to organize and access various shared resources from different servers.
5. How do I unmap a network drive?
To unmap a network drive, you can use the "net use" command with the "/delete" option in Windows or the "umount" command in Linux/macOS.
Tips for Effective Network Drive Mapping
- Use descriptive drive letters: Choose drive letters that clearly indicate the purpose of the mapped drive.
- Ensure proper permissions: Verify that you have the necessary permissions to access the shared resource.
- Regularly check drive availability: Ensure the network drive remains accessible and functional.
- Utilize password management tools: Store your network credentials securely using password management tools to avoid security risks.
- Consider using network drive mapping software: Several third-party tools offer advanced features and simplify the process of mapping network drives.
Conclusion: Unlocking Network Potential with Mapping
Mapping network drives remains a cornerstone of efficient network management, enabling users to seamlessly access and interact with shared resources. By leveraging command-line interfaces, users gain a powerful tool for streamlining workflows, enhancing productivity, and bolstering network security. Understanding the intricacies of mapping network drives empowers individuals and organizations to navigate the complexities of computer networks with ease and efficiency.

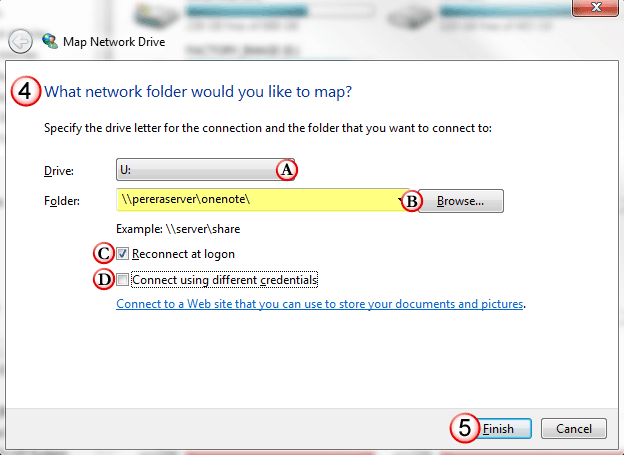
Closure
Thus, we hope this article has provided valuable insights into Navigating Networks with Ease: A Comprehensive Guide to Mapping Network Drives. We thank you for taking the time to read this article. See you in our next article!